

The strength of the encryption of a certificate is largely inherent to the encryption algorithm that was used to generate the private key. Hackers are intent on breaking these encryption algorithms: if the algorithm is out in the open, it can be combined with a public key to find the corresponding private key. Until recently, the RSA algorithm was most commonly used, but the ECC ot Elliptic Curve Cryptography algorithm is quickly growing in popularity. This algorithm can create a much smaller key while not losing any streneth when comoared to the much larger RSA keys. For instance, an ECC key of 228 bits is just as safe as an RSA key of 2380 bits.

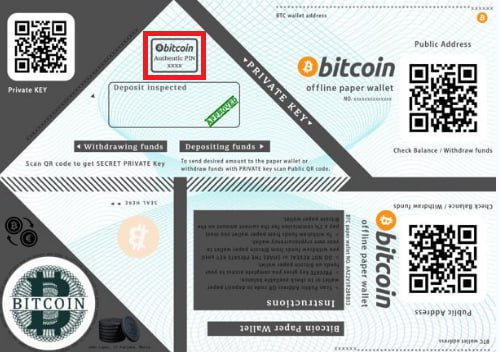
Explore private key to check Bitcoin addresses with balance

Please, fill form